Polyguard Key Technologies
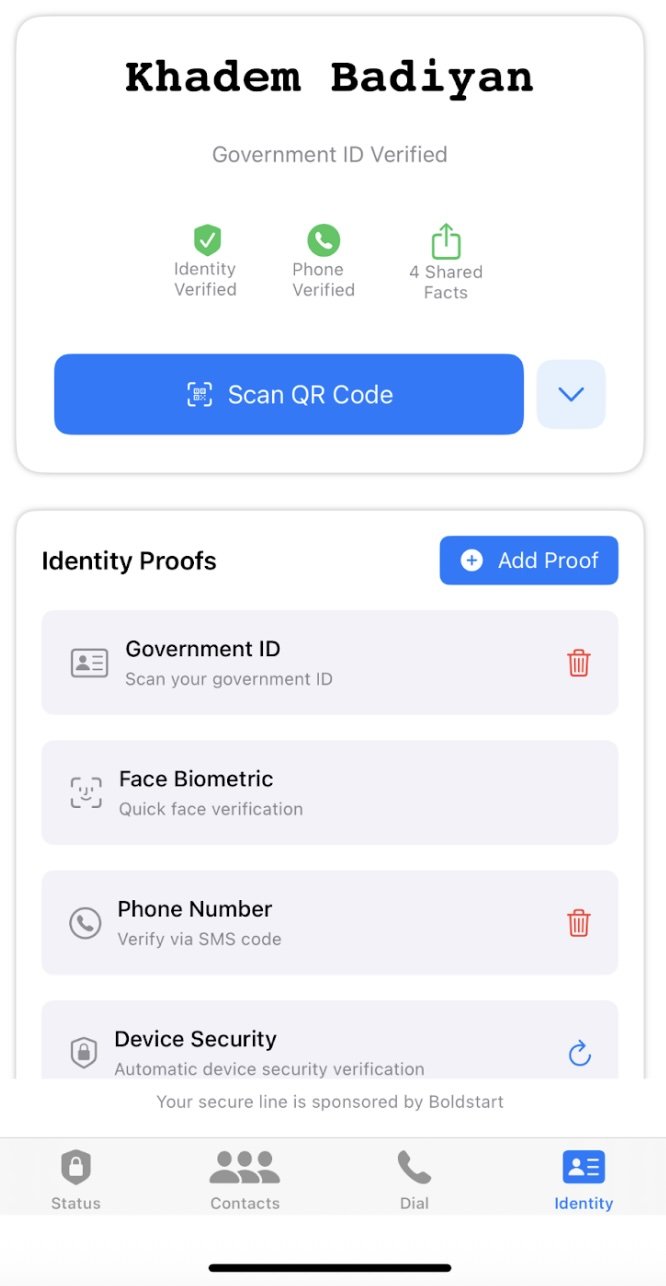
Personal Credential Store
Each user's verified identity is securely stored on their own mobile device using a personal credential store architecture. This approach prioritizes privacy and minimizes centralized risk by ensuring that sensitive identity data never needs to be aggregated in the cloud.
Key Technical Details:
Local Storage with Hardware-Backed Encryption:
Identity proofs — including biometric data, verified documents, and associated metadata — are encrypted and stored locally on the user’s device. Each credential is encrypted using a unique key that is generated and securely stored within the device’s hardware enclave (e.g., Apple Secure Enclave or Android TEE).Application-Scoped Access Control:
These encryption keys are bound to the Polyguard application, meaning they cannot be accessed by other apps, the operating system, or even Polyguard’s own cloud services. Only the authenticated Polyguard app instance running on the original device can decrypt and use these credentials.No Central Aggregation:
Unlike traditional identity providers that store personal data in centralized databases — creating attractive targets for attackers — Polyguard avoids aggregating user identity data in the cloud. This reduces the risk of large-scale breaches and ensures that each user remains in control of their own verified identity.
By combining secure local storage with application-scoped cryptographic protections, Polyguard significantly raises the standard for privacy and data security in identity verification.
Device Tamper-Proofing with Hardware Attestation
Polyguard employs Apple's App Attest framework to ensure the integrity of its mobile application and the authenticity of the devices on which it operates. This integration provides a robust mechanism to detect and prevent unauthorized modifications and usage.
How it works:
Secure Key Generation: During user registration, the Polyguard app generates a unique cryptographic key pair within the device's Secure Enclave. This key is inaccessible to the application itself, safeguarding it against extraction or misuse.
App Integrity Verification: The app creates an attestation that includes a hash of its binary and other relevant data. This attestation is signed by Apple, confirming that the app is genuine and unaltered.
Device Authenticity Assurance: The attestation process also verifies that the app is running on a legitimate Apple device. This step is crucial in preventing the use of emulators or jailbroken devices that could compromise security.
Payload Validation: For each critical operation, the app generates assertions that are cryptographically signed using the attested key. These assertions ensure that the data sent to Polyguard's servers has not been tampered with during transit.
By leveraging App Attest, Polyguard adds an additional layer of security, ensuring that only authentic, unmodified applications on genuine devices can interact with its services. This approach significantly reduces the risk of fraud and unauthorized access.
AI-Strong Biometric Verification
Polyguard’s biometric verification system is built to withstand the latest advances in synthetic media and presentation attacks. By leveraging 3D sensing capabilities in modern smartphones and combining them with secure execution environments, Polyguard ensures that biometric authentication is both accurate and resilient to spoofing.
Core Technologies and Protections:
3D Depth Sensing (LIDAR / Time-of-Flight):
Polyguard uses the smartphone’s front-facing depth sensor to capture a three-dimensional scan of the user’s face. This confirms the presence of a real human subject, rather than a flat image or a video replay. Devices with Apple FaceID or equivalent Android 3D sensing hardware are fully supported.On-Device Validation:
All biometric capture and liveness detection is performed on the device itself. Combined with Polyguard’s device tamper-proofing, this prevents external manipulation or injection of synthetic video streams via virtual cameras or emulators.Liveness & Anti-Spoofing Checks:
The biometric engine actively detects signs of spoofing attempts, including photo presentation, screen replays, and 2D masks. Depth cues, motion parallax, and illumination changes are evaluated in real time to confirm a live subject.Cryptographic Binding:
A successful facial verification is cryptographically bound to the session and device context, ensuring that verified identity cannot be reused or replayed in a different environment.
By combining hardware-enforced integrity with AI-driven biometric analysis, Polyguard ensures that biometric identity verification is not only convenient, but also resistant to modern impersonation tactics — including deepfakes, photo attacks, and avatar-based fraud.
“There are more than 1 billion ePassports issued currently, by 174 countries as of December 2024.”
Document Proofing
Polyguard combines third-party intelligence with in-house verification capabilities to deliver rigorous, globally scalable document proofing.
We integrate with Veriff, a best-in-class identity verification provider, to support a broad array of documents from across the globe. At the same time, for the most secure and tamper-resistant document types — such as ePassports and RealIDs — Polyguard performs direct, on-device verification using the smartphone’s NFC chip. This allows us to read cryptographically signed data embedded within the document’s secure chip, ensuring both the authenticity of the document and a high-confidence match to the individual’s biometrics and biographical information.
Coverage and Capabilities
Countries Supported:
Identity documents from over 230 countries and territories are accepted and validated through our integration with Veriff.Document Types Supported:
Over 12,000 unique government-issued identity documents, including:National ID cards
Passports and ePassports
Driver’s licenses
Residence permits
Travel visas
High-Assurance Document Verification (NFC):
For NFC-enabled IDs like ePassports and RealIDs, Polyguard performs secure element reading directly from the embedded chip — verifying both the digital signature and the biometric match without relying on third-party services.
Fraud Scoring by Document Type
Different document types carry different levels of inherent trust. A government-issued passport with embedded cryptographic data offers significantly stronger verification guarantees than a physical driver’s license or photo upload. Polyguard’s system automatically adjusts fraud risk scores based on document type, issuance country, and real-time verification confidence — enabling more accurate, context-aware decisions across hiring and onboarding workflows.
Business Records Affidavits
Polyguard ensures that each identity verification is supported by a legally admissible Business Records Affidavit, providing a robust foundation for compliance and legal defensibility.
A Business Records Affidavit is a sworn statement by the custodian of records affirming the authenticity and accuracy of business records. In legal proceedings, such affidavits are commonly used to admit business records into evidence without requiring the custodian to testify in person.
Key Features:
Immutable Audit Logs: Each secure meeting generates a cryptographically signed audit log, detailing the identity verification process, including methods used, timestamps, and outcomes.
Affidavit Generation: These audit logs are used to create Business Records Affidavits, which are signed by the custodian of records and notarized, affirming the records' authenticity.
Legal Admissibility: The affidavits comply with legal standards for admitting business records into evidence, facilitating their acceptance in court proceedings.
Accessibility: Affidavits are readily available through the Polyguard dashboard, linked directly to the corresponding audit logs for ease of retrieval.
By providing Business Records Affidavits, Polyguard offers clients a reliable means to demonstrate the integrity of identity verification processes, supporting legal compliance and enhancing trust in the system's security measures.
Location Proofing
Polyguard captures coarse-grained location signals to provide additional context and strengthen identity verification without compromising user privacy.
Location data is collected through multiple channels, including GSM network information, GPS readings, Wi-Fi SSID signatures, and IP address analysis. These signals are gathered both at the device level — via the tamper-evident mobile client — and at the network layer to ensure consistency and authenticity.
Importantly, all location data is collected in compliance with applicable privacy regulations (such as GDPR and CCPA). Only the minimum necessary information is captured, avoiding precise tracking while still enabling effective fraud detection and proof of presence.
Location proofing supports anomaly detection (e.g., impossible travel scenarios, unexpected geo-patterns) and reinforces trust decisions in a privacy-conscious manner.
Certainty Scoring
Polyguard is not a detection platform. In the synthetic age, where the line between real and artificial identities is increasingly blurred, we operate with a "default deny" posture toward any unverified identity.
Rather than relying on outdated fraud scoring models that attempt to detect anomalies after the fact, Polyguard provides a certainty score — a measure of how strongly a user’s identity has been verified based on cryptographic proofs and real-time biometrics.
Certainty scoring incorporates multiple independent signals, including:
Type and quality of the identity document presented
Results from document and identity proofing
Number and pattern of repeat identity proofing attempts
Validation against trusted third-party databases
Real-time facial biometric match distance and liveness results
Hardware attestation status, including repeat device certification attempts
Continuity of location signals across interactions
The certainty score provides administrators with clear, actionable insight into the trustworthiness of each verified participant — enabling confident decisions without relying on subjective or probabilistic fraud models.
Fine-Grained Trust Protocol
In today’s dynamic threat landscape, trust must be adaptive. Every organization — and every role within it — faces distinct risks. Polyguard’s fine-grained trust protocol extends traditional scoped authorization by introducing context-aware proof requirements that can be customized per role, per event, or per verification workflow.
Administrators, recruiters, and security analysts can easily define adaptive trust policies that specify exactly what proofs are required based on the sensitivity of the interaction and the threat environment.
Configurable parameters include:
Setting minimum certainty score thresholds for identity acceptance
Restricting verified participants to specific geographic regions based on location proofing data
Excluding lower-trust identity document types from approval flows
This architecture allows organizations to dynamically align identity verification policies with operational risk — providing strong, role-specific protection against synthetic, impersonated, or compromised identities.
PG Presence
Polyguard Presence extends verification beyond a single moment in time. By continuously anchoring verified identities to repeat interactions, devices, and contexts, PG Presence provides proof of ongoing authenticity.
Key Capabilities:
Persistent Identity Signals: Links verified users to their trusted device and biometric proofs, ensuring the same individual is recognized across sessions.
Continuity Tracking: Detects abnormal patterns (e.g., frequent device swaps, sudden location jumps) that may indicate impersonation or account takeover.
Contextual Trust: Builds cumulative trust scores as users re-verify over time, enabling smoother repeat interactions without lowering security.
Adaptive Defense: Makes it exponentially harder for deepfakes, synthetic identities, or one-time spoofing attacks to gain long-term credibility.